In this article, I will try to explain Azure Service Principal which is one of the concepts I believe should be known well.
What is Azure Service Principal?
Azure has “Service Principal” concept with a service account. This concept equals to a service account in Windows and Linux operating systems. These accounts generally use to run a particular task, web application pool or SQL Server service.
Azure Service Principal is a security identity created to access a specific Azure resource by user-created applications, services and automation tools. In this context, it allows you to provide sufficient permission and scope for the transactions to be performed within Azure source. Because It has the minimum principle of authorization to run tasks, that is important you should not use your own account to performed the tasks. In this way, Service Principal allows you to increase level of security.
For example; You can change pricing tier of a virtual machine or a service using an application with minimum authorization without using Azure portal. You will need service principal in such cases.
You can create Service Principal for as many application and services as needed.
How can create Azure Service Principal ?
You can use Azure portal, powershell with AzureAD and Azure modules to create Azure Service Principal. In this article, we will see how create service principal on Azure portal.
You should sign in to Azure portal using your Azure account to create service principal of your application on your Azure AD tenant.
Select App registirations >> New registration on Azure Active Directory.
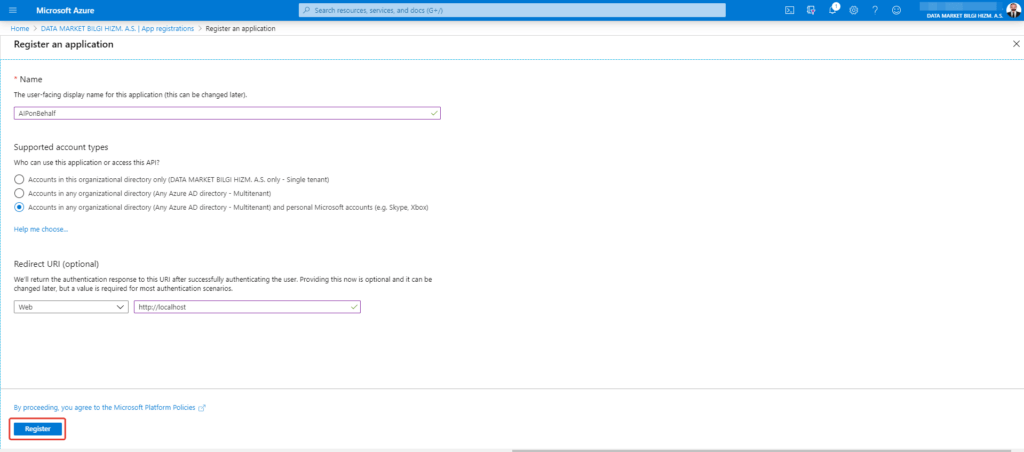
Create the name of application and select the supported account type. Then choose the type of application as a web under Redirect URI. ( If your application needs defined redirect URI, you can fill out this section.)
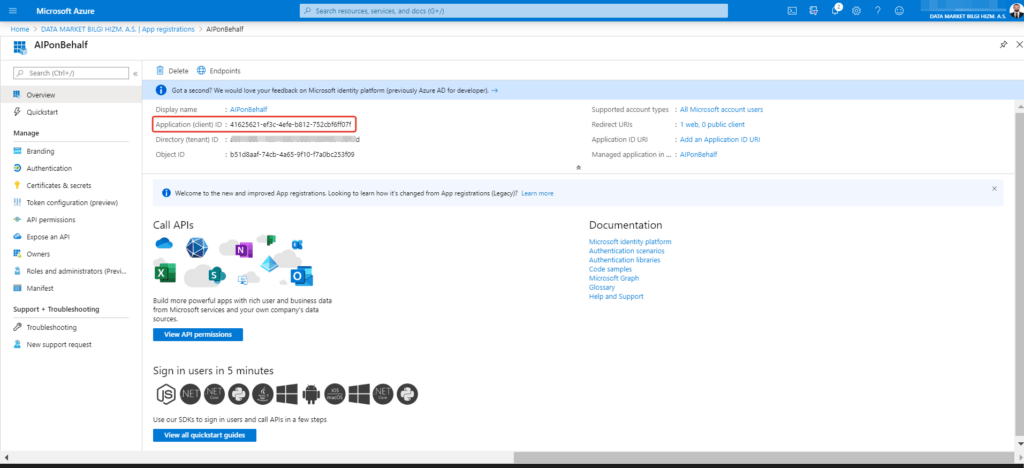
You can see application details after registiration of application on Overview page. Copy the Application ID (Client ID) information somewhere to use later.
Select New client secret in Certificates & Secrets page to create client secret.
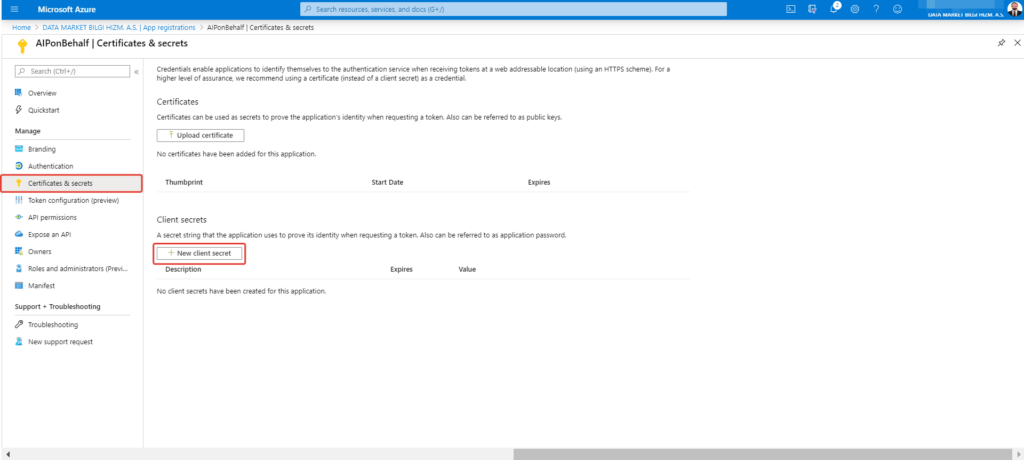
Select Add after fill out defination and date of expiration information of client secret.
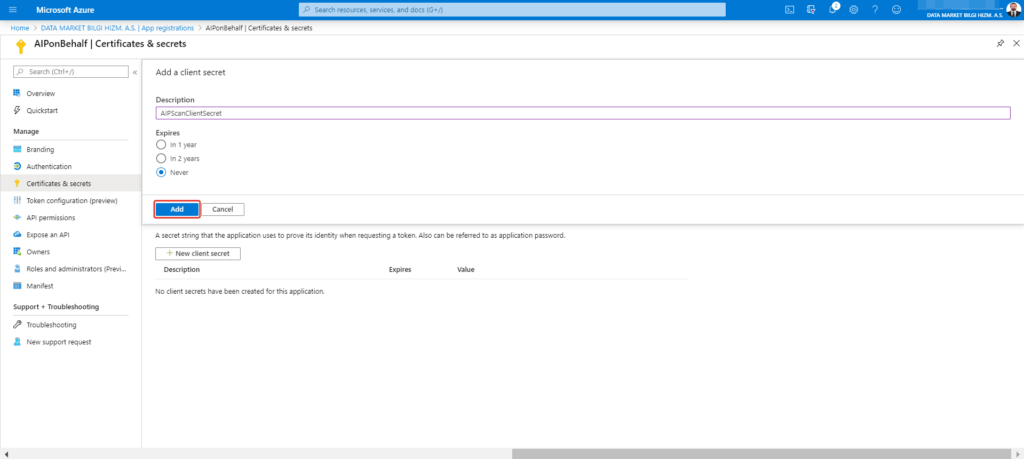
Copy the created secret value somewhere to use later. If you do not copy this value, you will never retrieve it. It provides to service principal’s login the application with created secret application id.
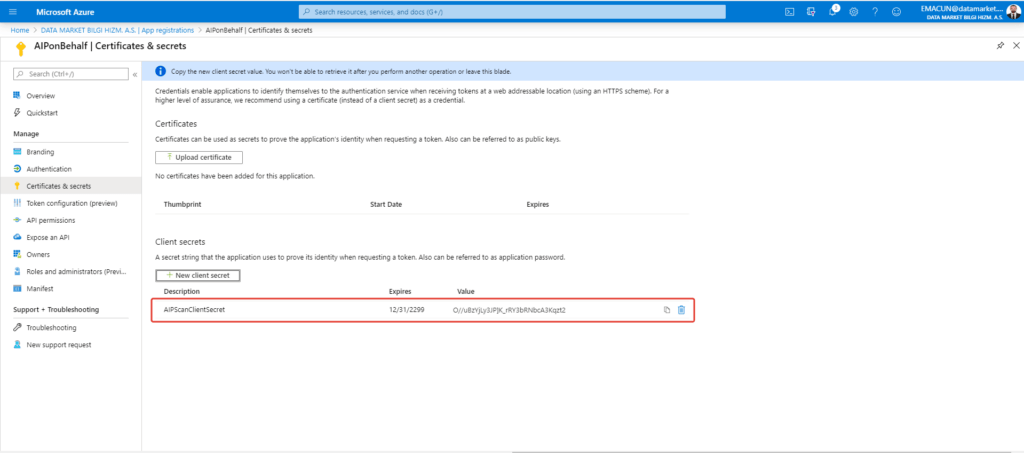
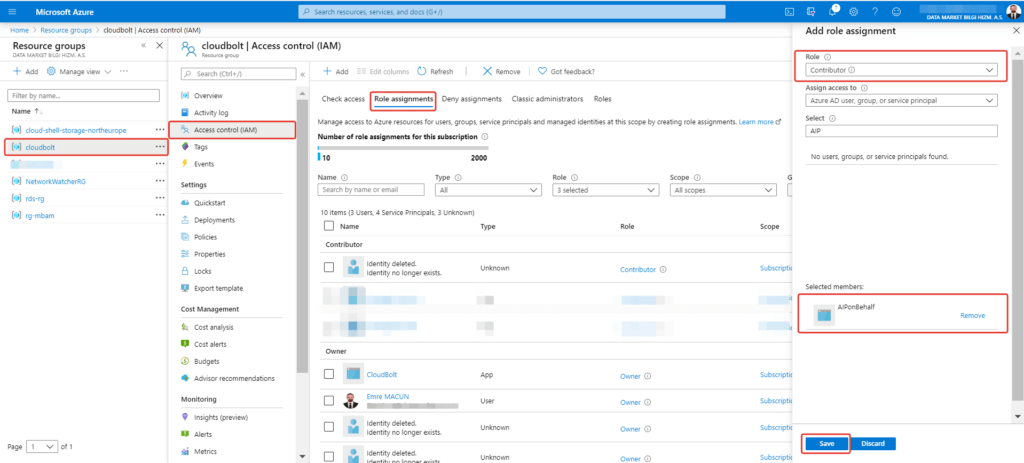
If you want to allow the application access resources under Azure subscription using service principal, you must define permission to service principal under particular resource or subscription.
Select related resource group in Resources Groups to define authorization of service principal on particular resource.
Select Access Control (IAM) >> Role Assigment under chosen resource group. Then select Add and choose your service principal to assign a role