What is Azure Key Vault?
Azure Key Vault is a service that has developed for applications and users to manage their secrets. In modern applications, it is generally not recommended to keep in-app secrets to protect against current attacks and vulnerabilities. So it makes sense to use a Vault to manage our secrets. In this way, people who develop the software leave the project or capture application source codes, etc. Even in situations, there is no vulnerability.
With Azure Key Vault, we can manage Secrets, Keys, and Certificates. In this way, we do not need to develop any protection algorithm for any of our secrets in the application. The key vault service uses Azure Active Directory (AAD) for Authentication. It uses Rol Based Access Control (RBAC) for authorization. In this way, we can authorize a user to read a secret, but we do not have to authorize to delete or change it. Azure Key Vault service can summarize metrics such as which secret, how much key is used and where it is called from. If we want to write these logs to a storage, we can turn them into dashboard on Azure monitor. In addition, Azure provides us a great convenience for us to work integrated with other Azure services. With a single confirmation, we can determine how it interacts or authorizes with other azure services.
Azure Key Vault Secrets
In our key vault, usually the secrets section is the most used feature. As Secret, we can contain connection strings, passwords or tokens of our application. Key vault secrets are stored and managed as passwords. When the data is saved, Key Vault stores and manages this data as octal arrays (8 bit bytes). Each is a maximum of 25k bytes in size. It then returns an ID to us so we can call this secret again. Of course, if we want to increase the security of our secrets, in addition to this encryption of Key Vault, we can increase our security layer by sending an encrypted key vault within the application. The user can specify the data type when creating a secret. It provides convenience for us when capturing and managing this data.
Secret Properties
Expiration Date : While creating a secret, we can restrict the use of this secret after a certain time. This feature comes accessible forever by default.
Not Before : We created a secret, but if you don’t want anyone to use it right now, you can set a rule with this feature that can be used after 1 week.
Accessable : With this feature, your secret has been created, but you can restrict the accessibility of the secret if you do not want anyone to use it.
In addition, we can display parameters such as the creation date of the secret and the modified dates.
Secrets Access Control
Access control for the Azure Key Vault service is provided only for that vault. This means if you authorize X to read secrets, they can read all secrets. If you want to separate some secrets, you have to create another one for this service. It is generally recommended to create Key Vaults according to the scenario here. Access Rights:
- Get: Reading a specific secret
- List: Bringing information to all secrets held in that key Vault
- Set: Create a secret
- Delete: Delete a secret
- Recover: Bring back a deleted secret
- Backup: Backing up a secret in Key Vault
- Restore: Bringing back a backup secret
Key Vault Cheatsheet
Some commands for Key Vault that we can use in Azure CLI are as follows:
List All Azure Key Vaults = az keyvault list [–resource-group] [–subscription]
KV Deletion = az keyvault delete –name
KV Creation = az keyvault create –name –resource-group –subscription –location –enable-soft-delete –tags
KV Feth Information = az keyvault show –name –resource-group –subscription
Secret Fetch Information = az keyvault secret show –id –name –subscription –vault-name
Secrets List = az keyvault secret list –vault-name
Recovering a Deleted Secret = az keyvault secret recover –id –name –subscription –vault-name
Secret Creation = az keyvault secret set –vault-name “<your-keyvault-name>” –name “MySecret” –value “Success!”
Secret Deletion = az keyvault secret delete –id –name –subscripotion –vault-name
Fetch Key Info = az keyvault key show –id –name –subscription –vault-name
List Keys= az keyvault key list –vault-name
Recover Key = az keyvault key recover –id –name –subscription –vault-name
Key Creation = az keyvault key create –name –vault-name
Key Deletion = az keyvault key delete –id –name –subscripotion –vault-name
Key Vault Usage Scenarious
In a .Net Application we can use the SDK if we want to bring a secret from our Key Vault, or use the REST API calls if we want. To briefly mention the SDK usage example, we can start by installing the following 3 nuget packages in our application:
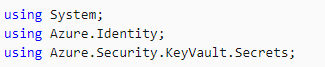
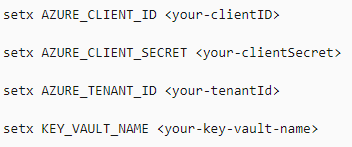
Then we create a Service Account to access our Key Vault in Azure Active Directory and we determine the information of our Service Account as environment variable in our application;
Then, we create our KV url in our controller as follows.
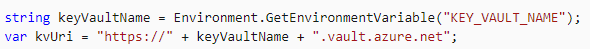
After this step, we can create our client for our KV as follows;
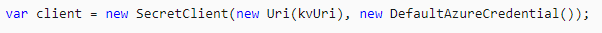
After this step, we can create a secret if we want. If we want, we can use a secret in our Vault in the application as below.
